Vulnerability Assessment recommends disabling Remote Admin Connections
SSMS 17 has the handy ability to run quick Vulnerability Assessments against your database.
Scan for Vulnerabilities
One of the Vulnerability Assessment checks looks to see if the Dedicated Administrator Connection, otherwise known as the “DAC”, is enabled for remote access. The DAC, as indicated by the name, is a dedicated connection that members of the sysadmin server role can use to connect to the SQL Server when it is otherwise unresponsive. It’s very useful if the server itself is experiencing high CPU, allowing a sysadmin to determine the underlying cause of the non-responsiveness prior to (typically) rebooting the server. Being able to access the DAC from the network, i.e. via a remote connection, is probably the most useful scenario since most of the time you cannot login to the affected server via Remote Desktop or even at the physical console if CPU usage is pinned at 100%.
The Vulnerability Assessment performs the following check against the SQL Server instance, looking to see if the DAC is enabled for remote connections:
|
1 2 3 4 5 6 7 |
SELECT CASE WHEN EXISTS (SELECT * FROM sys.configurations WHERE NAME = 'remote admin connections' AND Cast(value AS INT) = 1) THEN 1 ELSE 0 END AS Violation |
If you’ve configured the DAC for remote connection, it reports that as a “medium” risk failure:
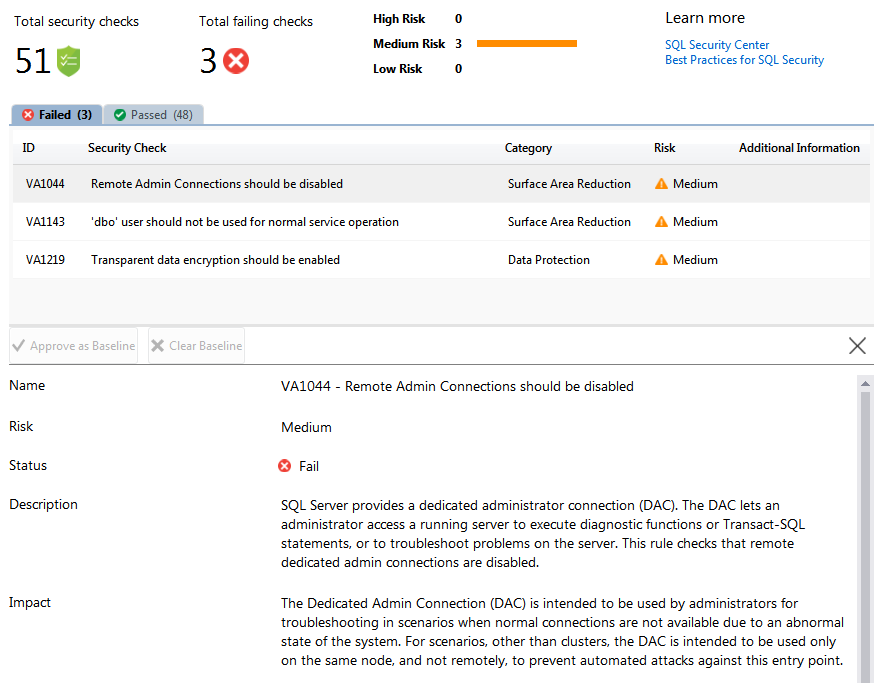
dac remote admin connection failure
Certainly, you’d want to ensure the port for the DAC is not available to the Internet, but hopefully if you’re reading this blog you already know how silly it would be to open SQL Server to the Internet.
Assuming you don’t have the port open to the Internet, it’s very likely the DAC will not be of any use at all if you disable Remote Admin Connections as advised in the Vulnerability Assessment. My advice is to ignore this warning completely and configure the DAC to allow remote connections. Microsoft Technet has documentation about using the DAC, and says to configure it for remote connections by logging onto the server locally first, then configuring SQL Server to allow remote DAC connections, which seems a bit like putting the cart before the horse.
Agree? Disagree? Have I missed something? Let me know in the comments below.

[…] Hannah Vernon points out a SQL Server Management Studio Vulnerability Assessment check which seems some…: […]
[…] Microsoft also provides an excellent tool for looking at vulnerabilities on a database level with the SQL Vulnerability Assessment tool. Be aware, it may advise you to disable the Remote Admin Connection, which is something I’m mostly against, as discussed in this post. […]
There has been a few cases where the local SQL Server was spiked to 100 % cpu. The DB was the issue. However, You could not login to the DB nor RDP to the server with the CPU at 100%. You need the DAC in this 1 rare instance to connect remotely and run sp_who2 to find and kill the bad process spid.